Mapping Cybersecurity Frameworks
by Mark Alabanza, MBA, BSAc, CISA
2016 Oct 01
Click here for a live demo of the visualization. It takes a while to load the 6,329 records of the data table. Please let me know of any other issues in loading the web page.
The frameworks
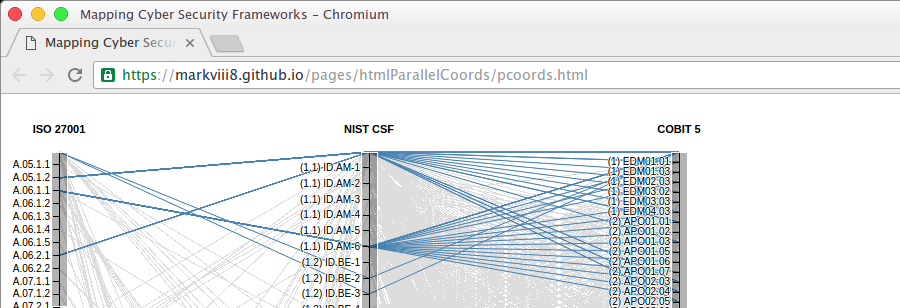
Popular frameworks applicable to cyber security include ISO/IEC 27001, the NIST Cybersecurity Framework, and ISACA’s COBIT 5. This visualization shows the mapping of prescribed activities of each framework to the others.
The mapping
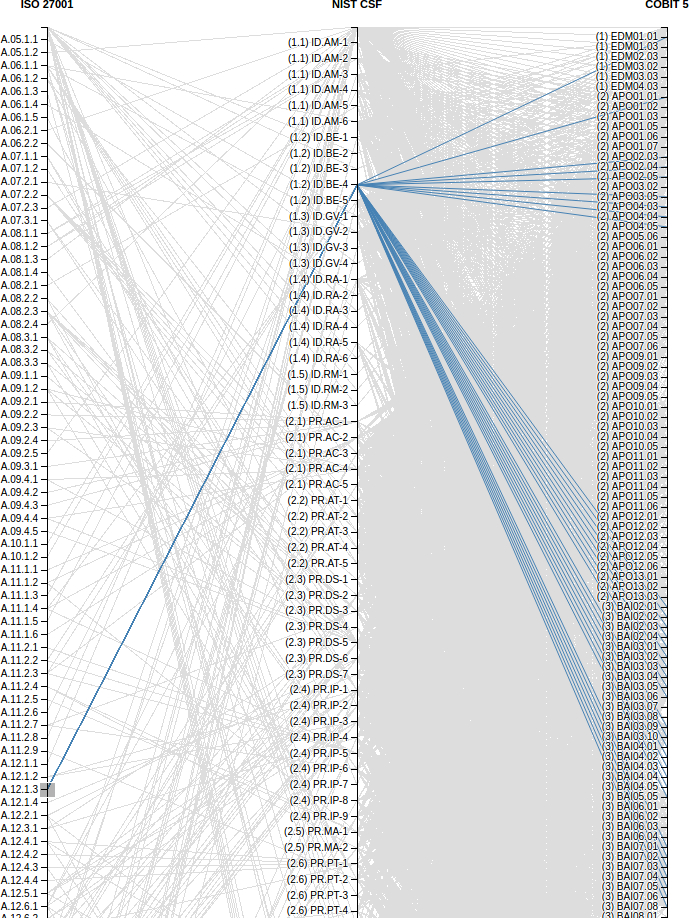
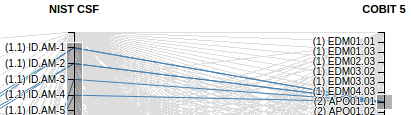
In the image below, ‘ISO/IEC 27001 A.12.1.3 Capacity Management’ is mapped to ‘NIST Cyber Security Framework ID.DE-4 Dependencies and critical functions for delivery of critical services are established.’ That, in turn, is mapped to the following 33 COBIT 5 Process Enablers.
- EDM01.01 Evaluate the governance system.
- APO01.01 Define the organisational structure.
- APO02.03 Define the target IT capabilities.
- APO02.04 Conduct a gap analysis.
- APO02.05 Define the strategic plan and road map.
- APO03.05 Provide enterprise architecture services.
- APO04.03 Monitor and scan the technology environment.
- APO04.04 Assess the potential of emerging technologies and innovation ideas.
- APO04.05 Recommend appropriate further initiatives.
- BAI02.01 Define and maintain business functional and technical requirements.
- BAI02.02 Perform a feasibility study and formulate alternative solutions.
- BAI02.03 Manage requirements risk.
- BAI02.04 Obtain approval of requirements and solutions.
- BAI03.01 Design high-level solutions.
- BAI03.02 Design detailed solution components.
- BAI03.03 Develop solution components.
- BAI03.04 Procure solution components.
- BAI03.05 Build solutions.
- BAI03.06 Perform quality assurance.
- BAI03.09 Manage changes to requirements.
- BAI03.10 Maintain solutions.
- BAI04.01 Assess current availability, performance and capacity and create a baseline.
- BAI04.02 Assess business impact.
- BAI04.03 Plan for new or changed service requirements.
- BAI04.04 Monitor and review availability and capacity.
- BAI04.05 Investigate and address availability, performance and capacity issues.
- BAI05.05 Enable operation and use.
- BAI07.02 Plan business process, system and data conversion.
- BAI07.03 Plan acceptance tests.
- BAI07.04 Establish a test environment.
- BAI07.05 Perform acceptance tests.
- BAI07.06 Promote to production and manage releases.
- BAI07.08 Perform a post-implementation review.
Walkthrough of one sample
Here is how the visualization isolated the mapping for A.12.1.3.
When the mouse pointer is close to one of the vertical lines, it changes to a crosshair image.
Bring the crosshair to the tick mark (or group of consecutive tick marks) that would be isolated.
Hold down the right mouse button and drag the pointer to create a grey rectangle on the selection.

 The grey rectangular selection can be moved to another tick mark (or group of tick marks).
Put the mouse pointer on the current grey rectangular selection until it changes to a 'move' image.
Hold down the right mouse button and drag the 'move' image and rectangle to the desired tick mark/s.
The grey rectangular selection can be moved to another tick mark (or group of tick marks).
Put the mouse pointer on the current grey rectangular selection until it changes to a 'move' image.
Hold down the right mouse button and drag the 'move' image and rectangle to the desired tick mark/s.
 Increase or decrease the height of the grey rectangular section by dragging its top margin or bottom margin.
Selections can be marked on each of the three vertical lines individually or simultaneously.
Increase or decrease the height of the grey rectangular section by dragging its top margin or bottom margin.
Selections can be marked on each of the three vertical lines individually or simultaneously.
Next steps
Selections can be improved by simply putting the mouse pointer on a text or a line.